A VLAN, or Virtual Local Area Network, is a logical network that allows devices connected to physically different LANs to communicate. VLANs can be created on a single switch or across multiple controllers and configured based on port, MAC address, or protocol. VLANs provide network segmentation, improve security, and enhance network performance.
A VLAN uses a unique VLAN ID or number to differentiate and isolate network traffic. Switches are configured to identify the VLAN traffic using the VLAN ID. This enables the controller to forward traffic within the same VLAN while blocking traffic from other VLANs.
VLANs offer several benefits for network infrastructure, including:
Reduced broadcast domain size
VLANs are used to segment a network into smaller broadcast domains. This reduces the amount of broadcast traffic on the web, improving network performance.
Enhanced network security
VLANs can isolate sensitive data and devices, preventing unauthorized access from other VLANs. This helps to improve the overall security of the network.
Scalability
By creating logical segments, VLANs allow for easier management of large networks. Adding new users or devices can be easily accommodated by allocating new VLANs.
Improved network performance
Isolating certain types of network traffic and optimizing the data transfer rates within VLANs can significantly improve network performance, resulting in faster and more reliable data transfers.
Recommended Reading: Data Center Network Architecture
There are several types of VLANs, including:
Port-based VLANs
This type of VLAN assigns a logical network to a specific port on a switch. Devices connected to that port are then transferred to the assigned VLAN.
MAC address-based VLANs
This type of VLAN assigns a logical network based on the device’s MAC address.
Protocol-based VLANs
This type of VLAN assigns a logical network based on the protocol used for network communication, such as TCP/IP or FTP.
Dynamic VLANs vs. Static VLANs
Dynamic VLANs are configured to automatically assign devices to the appropriate VLAN based on criteria, such as MAC address, while static VLANs are manually configured. Dynamic VLANs are useful in environments where devices are frequently moved or added. Static VLANs are typically used to isolate specific types of traffic, such as VoIP or video conferencing.
Virtual Local Area Networks (VLANs) effectively segment network traffic based on different requirements, such as departments, projects, or security requirements. VLANs provide flexibility, scalability, and security by allowing multiple logical networks to coexist on a single physical network infrastructure.
To configure VLANs effectively on a network device, you must consider the specific requirements and capabilities of the device, as well as the network topology and traffic patterns. VLANs can be configured on a router, switch, or firewall with appropriate VLAN capabilities.
To configure VLANs on a router, you need to follow these basic steps:
Enable VLANs by issuing the “vlan database” command.
Create VLANs by specifying VLAN IDs and names.
Assign ports to VLANs by issuing the “switchport access vlan” command on relevant interfaces.
Configure VLAN routing by creating VLAN subinterfaces or using a router-on-a-stick configuration.
Configuration parameters that need to be considered for VLANs are VLAN ID, VLAN name, MTU size, IP address assignment, VLAN interfaces, VLAN membership modes, and VLAN spanning tree protocol.
Configuring VLANs on Ethernet ports requires careful consideration of VLAN membership modes, security policies, and traffic types. VLAN membership modes can be access, trunk, or hybrid, each with specific properties. Access mode is used for a single VLAN, while trunk mode is used for multiple VLANs. However, hybrid mode can accommodate access and trunk traffic on the same port.
VLAN tagging is an important consideration when configuring VLANs on Ethernet ports. VLAN tagging enables multiple VLANs to be transmitted over a single physical link without interfering with one another.
Security policies such as port security, port-based authentication, and MAC address filtering should also be implemented to secure the traffic between VLANs.
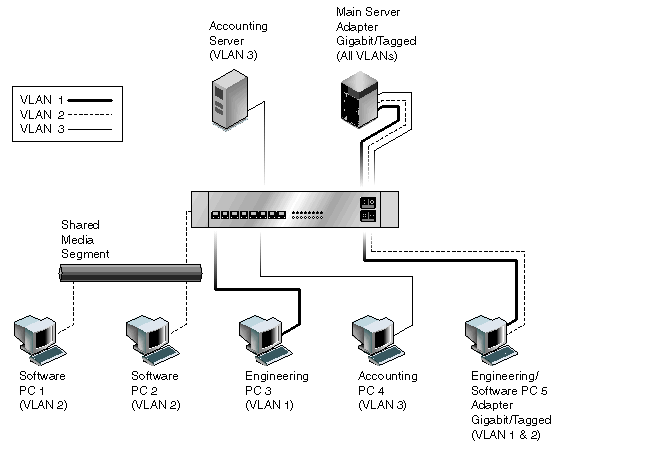
VLAN tagging is a technique that separates VLAN identification information from the data carried on the network. VLAN tagging enables switches, routers, and other network devices to distinguish between VLANs.
VLAN tagging adds a four-byte tag to each Ethernet frame, providing additional information identifying which VLAN the frame belongs to. When a tagged frame is transmitted, the title is inserted into the Ethernet frame header, and the receiving device uses this tag to distinguish between VLANs.
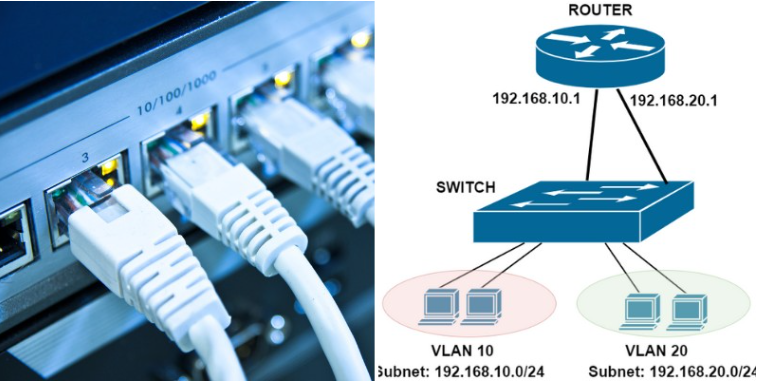
VLAN routing is an essential aspect of VLAN configuration, enabling communication between VLANs by forwarding packets from one VLAN to another. Some methods for VLAN routing are inter-VLAN routing via router subinterfaces, router-on-a-stick, and Layer 3 switches.
Inter-VLAN communication across a network can be managed using different methods. These methods include routing on a stick, switching virtual interfaces, or a Layer 3 or multilayer switch. However, the routing method chosen should be efficient and secure to ensure optimal network performance.
Recommended Reading: What is a Data Center Network? How to manage a data center network
VLANs are a critical component in modern networking environments. They allow network administrators to segment traffic, improve performance, and enhance security. However, like any other network technology, VLANs are susceptible to issues and errors that can reduce their functionality and performance. Let’s discuss the most common issues network engineers face and suggest troubleshooting steps to diagnose and mitigate those issues.
One of the most common issues network engineers encounter is misconfiguration of VLANs. Incorrect VLAN configuration can result in network segmentation issues, connectivity issues, and performance degradation. The first step in troubleshooting VLAN configuration issues is to verify that the correct VLAN configuration is in place. This can be done using tools such as show VLANs, interfaces, and interface trunk commands. If the VLAN configuration is correct, the problem may be caused by a misconfiguration of the switch port. In this case, the switch port should be checked for incorrect access mode or trunk mode configuration.
VLAN connectivity issues are another common problem that network engineers face. Various factors, such as incorrect VLAN tagging, VLAN configuration, network congestion, or physical issues, can cause VLAN connectivity issues. The first step in troubleshooting VLAN connectivity issues is ensuring the network equipment works correctly. This can be done using a network monitoring tool like Wireshark or PRTG. Additionally, the network engineer should check the VLAN configurations on the switch and ensure that the network topology is correctly configured.
VLAN membership management is crucial for correctly segmenting and managing network traffic. The incorrect membership of VLANs can cause connectivity issues and security vulnerabilities. The first step in managing VLAN membership is to ensure that the correct VLAN is associated with the right switch port. This can be done by using the show VLAN command on the switch. The network engineer should monitor the traffic to ensure it is correctly tagged and routed.
Broadcast traffic can become a significant issue in VLANs, especially if the network is improperly configured. Broadcast traffic can cause congestion, slow network performance, and even lead to security vulnerabilities. One way to reduce broadcast traffic is to limit the number of devices in a VLAN. Additionally, VLAN pruning can control the network’s broadcast traffic.
VLAN security is essential for protecting a network from security threats and vulnerabilities. It’s crucial to implement the following security best practices to ensure VLAN security:
Use VLAN access control lists (ACLs) – VLAN ACLs allow network administrators to filter traffic based on MAC addresses, IP addresses, or protocols.
Segment critical traffic – Critical traffic such as servers, printers, and VoIP phones should be placed in separate VLANs to reduce the risk of security breaches.
Implement VLAN trunking protocols – VLAN trunking protocols such as VLAN tagging and VTP can help improve network performance and security.
Monitor network traffic – Network traffic should be monitored regularly to identify potential security threats or vulnerabilities.
Recommended Reading: Everything You Need to Know About Aggregation Switch
Virtual Local Area Networks (VLANs) have become an increasingly important tool for engineers designing and maintaining modern enterprise networks. By providing network segmentation and resource management, VLANs offer a powerful means of improving network efficiency and security.
The concept of trunking emerged due to the need to connect multiple switches within the same network. VLAN trunking allows network administrators to consolidate and distribute network traffic between switches using a single physical connection, maximizing system uptime and resilience.
VLAN tagging is another critical consideration in the use of VLANs. Tagging involves adding a unique identifier on each data packet. By adding a VLAN ID (VID) on each Ethernet frame header, switches can know which VLAN a packet belongs to. Tagging also helps network administrators determine which packages should be forwarded and which should be filtered. In classical Ethernet networks, frames transmitted from one port are broadcasted to every other port. VLAN tagging facilitates the partitioning of multiple broadcast domains, reducing broadcast transmissions.
In addition to improving network efficiency, VLANs can help network engineers manage their resources more effectively. For instance, VLANs can facilitate network segmentation, allowing different departments to allocate bandwidth, manage IP addressing, and effectively control network resource usage.
In Layer 3 networks, VLANs can be used to enable inter-VLAN communication. In other words, VLANs created on a switch can communicate with others on different buttons. Using Layer 3 switching, routing between VLANs can also be enabled using an IP address assigned to the VLAN interface.
Network segmentation is essential for creating isolated environments within a network to achieve resource management and control. With VLANs, network administrators can divide network areas or departments that require increased security and supervision. A network administrator can achieve greater traffic segmentation in a less complex network infrastructure by creating smaller broadcast domains. Segmentation allows for more targeted security solutions like firewalls and access control devices.
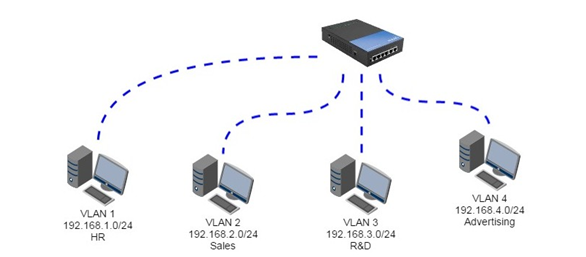
VLANs can be implemented in both single and multiple-switch environments. VLANs can be used in single-switch environments to designate different ports for different VLANs. This achieves the objective of traffic segregation, allowing for more excellent management and control of network traffic. VLANs can also be used in a single switch environment to connect different departments. For instance, creating VLANs for Finance, Sales, and Marketing can offer each department its unique broadcast domain, enabling fine-grained network resource management and enhanced security.
Finally, VLANs can enhance network security by improving the isolation of sensitive data and company-owned resources. By establishing VLANs within the network, system administrators can enforce security policies by controlling access to the VLAN through access control lists (ACLs). ACLs can restrict which IP addresses are allowed to communicate with specific VLANs in the network.
Moreover, VLANs can also help in optimizing network resource management. By segmenting the network traffic, administrators can better manage network resources by providing network capacity to where it is most needed. For instance, a department with heavy internet usage can be allocated more bandwidth capacity than other departments with fewer network traffic requirements.
Recommended Reading: Data Center & Cloud
As a network engineer, VLAN configuration is a critical task that should be done carefully and precisely. VLANs are groups of devices that are logically segmented and isolated on the network, and implementing VLANs in a networking environment can provide several benefits, such as increased security, improved traffic management, and simplified maintenance.
To ensure that VLAN configuration is done correctly, it is essential to understand the difference between VLAN numbers and VLAN IDs.
A VLAN number is a unique numerical identifier assigned to each VLAN in the network. In contrast, a VLAN ID is a user-defined name or label assigned to a VLAN, which is more convenient for users to work with than VLAN numbers.
Assigning VLAN IDs that are easy to remember and associated with their corresponding VLANs is essential. For example, setting the VLAN ID “Sales” to a VLAN that includes all sales department devices will be more straightforward than assigning a random number to the VLAN.
After assigning VLAN IDs, the next step in VLAN configuration is configuring the VLAN interfaces. VLAN interfaces define Layer 3 addresses for specific VLAN segments on the network. Each VLAN should have a unique interface assigned to it.
It is best practice to configure VLAN interfaces on the router and switch. The router will handle routing traffic between VLANs, while a switch can assist in directing VLAN traffic. By assigning an IP address to each interface, users on one VLAN can communicate with users on another VLAN.
Ensure that Inter-VLAN communication is well managed. Network performance is optimized when a multilayer switch is deployed, and inter-VLAN routing occurs inside the button rather than flowing through an external router. Networks with excessive inter-VLAN traffic must plan for the more extensive bandwidth utilization.
VLAN security is of utmost importance. Access Control Lists (ACLs) may restrict access to specific VLANs and control traffic flow within VLANs. ACLs may permit or deny access to specific VLANs based on a user’s IP address, MAC address, or port.
VLAN performance can be improved in a variety of ways. One approach is to segregate VLANs by function to reduce traffic congestion. Additionally, deploying smaller broadcast domains, such as IGMP snooping switches, can minimize multicast traffic. Another approach is to monitor the bandwidth usage of VLANs and upgrade them as necessary.
In conclusion, understanding VLAN numbers versus VLAN IDs, configuring VLAN interfaces, managing Inter-VLAN communication, securing VLANs with Access Control Lists, and optimizing VLAN performance are all critical practices that should be followed when configuring VLANs in a network environment. Using these best practices, the network engineer can ensure that VLAN implementation is done correctly and that the network is secure and efficient.
Recommended Reading: Everything You Need to Know about SFP Ports
A: VLAN stands for Virtual Local Area Network. It is a logical group of devices configured to communicate as if connected to the same physical local area network (LAN). VLANs use network switches to separate and isolate network traffic into different virtual networks.
A: VLANs work by adding a tag or label to each network packet that indicates the VLAN to which it belongs. Network switches use these tags to direct the boxes to the appropriate VLANs, ensuring that traffic is isolated and only reaches the intended devices.
A: VLANs offer several advantages, including improved network performance, enhanced security, and simplified network management. By segmenting network traffic, VLANs reduce congestion and improve overall network efficiency. They also allow network administrators to control resource access and enhance security by isolating sensitive data. Additionally, VLANs make managing and configuring networks easier, as changes can be made at the VLAN level rather than on individual devices.
A: There are two main types of VLANs: static and dynamic. The network administrator manually configures Static VLANs. Devices are assigned to a specific VLAN based on physical location or function. Dynamic VLANs, also known as VLAN Membership Policy Server (VMPS) or VLAN Trunking Protocol (VTP), allow devices to be automatically assigned to VLANs based on specific criteria, such as MAC address or user authentication.
A: VLANs work by configuring network switches to create and manage virtual networks. Switch ports can be assigned to specific VLANs, and devices connected to these ports become part of that VLAN. The switch then encapsulates traffic with the appropriate VLAN tags, allowing it to be routed between different VLANs.
A: By default, devices in different VLANs are isolated and cannot communicate directly with each other. However, network administrators can configure inter-VLAN routing to allow communication between specific VLANs using a router or layer 3 switches.
A: A VLAN tag is an additional information added to a network packet that identifies the VLAN to which the package belongs. It contains information such as the VLAN ID, which switches use to determine the appropriate VLAN for the box.
A: VLANs are virtual networks created within a physical LAN. While a physical LAN consists of devices connected to the same network segment, VLANs allow network administrators to logically group devices across different physical locations or network switches.
A: No, a device can only belong to one VLAN at a time. However, devices can communicate with devices in other VLANs through routing or configuring a machine to be a member of multiple VLANs through VLAN trunking.
A: VLAN trunk ports are switch ports configured to carry traffic for multiple VLANs. These ports use tagging to identify the VLAN to which each packet belongs so that it can be correctly routed to the appropriate VLAN.
A: Configuring a VLAN typically involves accessing the management interface of your network switch and creating a new VLAN. You can assign switch ports to the VLAN and configure additional settings or security measures.