——
Internet Group Management Protocol (IGMP) Snooping is an advanced network switch feature that optimizes multicast data traffic on a local area network (LAN). This technology enables a network switch to analyze IGMP messages and make intelligent forwarding decisions based on this information.
IGMP Snooping increases the efficiency of multicast traffic by restricting unnecessary forwarding of multicast traffic to all ports on a network. Instead, it ensures that the multicast traffic is forwarded only to those ports associated with an IP multicast group, thereby reducing unwanted network congestion.
Enabling IGMP Snooping in your network can lead to various benefits. It not only reduces unnecessary network traffic but also frees up network resources and improves overall network performance. Furthermore, it enhances the reliability and speed of applications that rely on efficient multicast delivery.
In a network switch, IGMP Snooping works by analyzing the IGMP messages between hosts and routers and maintaining a multicast group membership table. This table is then used to make intelligent forwarding decisions, ensuring that multicast traffic only reaches the necessary ports.
The Querier plays a crucial role in the operation of IGMP Snooping. It’s responsible for sending out IGMP queries to determine which hosts belong to which multicast groups. The responses to these queries are then used by the network switch to update its multicast group membership table.
——
Internet Group Management Protocol (IGMP) Snooping is a significant technique in networking that optimizes multicast traffic within a Local Area Network (LAN). It is a layer 2 switch feature that manages and controls multicast group memberships, thus enhancing the overall performance of the network.
IGMP Snooping optimizes multicast traffic by inspecting, filtering, and forwarding multicast streams to only those ports that belong to the multicast group. This selective forwarding of traffic significantly reduces unnecessary load on the network and boosts its efficiency.
In a virtual local area network (VLAN), unnecessary multicast forwarding can lead to network congestion. However, with IGMP Snooping, a switch can control multicast traffic by limiting the forwarding of such traffic only to the ports that have members of the multicast group.
IGMP Snooping improves bandwidth utilization by ensuring that multicast traffic is delivered only to the interfaces that have requested it. By reducing excessive multicast traffic, it makes more efficient use of the available bandwidth, thereby enhancing the overall performance of the network.
IGMP Snooping also contributes to network security by preventing multicast traffic from being forwarded to ports that do not have any multicast group members. This can prevent unauthorized access to multicast group data, thereby increasing the security of the network.
Fast Leave is another feature associated with IGMP Snooping. It allows a host to leave a multicast group instantly without waiting for the following query interval. This leads to quicker updates of the multicast group membership table and further enhances the efficiency of multicast traffic management.
——
Internet Group Management Protocol (IGMP) Snooping is a crucial networking technique that optimizes the handling of multicast traffic within a Local Area Network (LAN). The implementation and configuration of IGMP Snooping involve several steps, including enabling it on a network switch, setting up an IGMP Querier, supporting IGMPv3 for advanced multicast group management, configuring it on routed multicast networks, and ensuring its proper functionality in VLAN environments.
The first step in implementing IGMP Snooping involves enabling it on a network switch. This can usually be done through the switch’s configuration interface. Once enabled, the switch will start inspecting IGMP messages between hosts and routers, allowing it to make intelligent forwarding decisions based on this information.
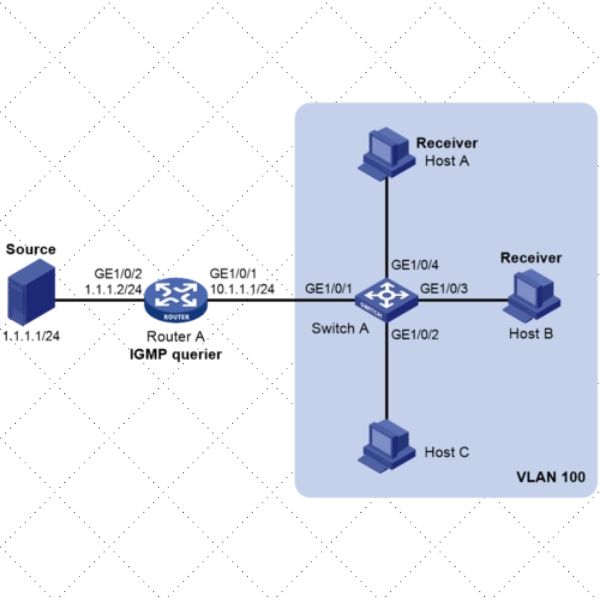
An IGMP Querier is responsible for sending out IGMP queries to determine which hosts belong to which multicast groups. Configuring an IGMP Querier is essential for efficient multicast communication as it allows the network switch to maintain an accurate multicast group membership table.
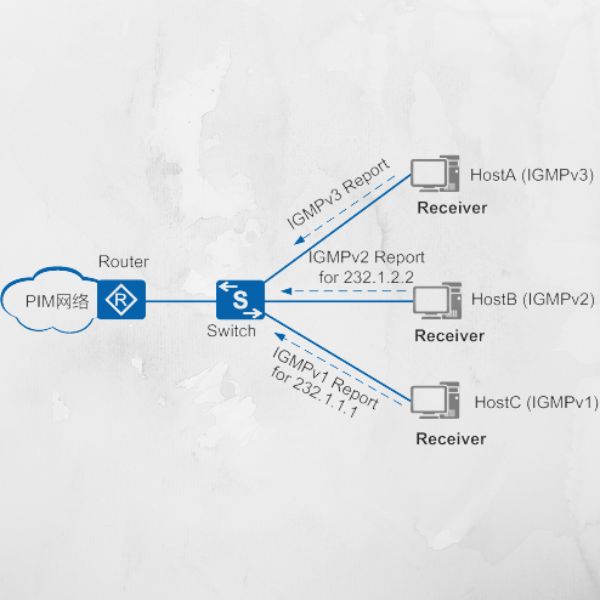
IGMPv3 is the latest version of IGMP and offers advanced features for multicast group management. By supporting IGMPv3, a network switch can handle situations where hosts belong to multiple multicast groups and can also support source-specific multicast, which adds another layer of efficiency to multicast traffic management.
In a routed multicast network, IGMP Snooping can be configured to ensure that multicast traffic is forwarded correctly across multiple network segments. This involves setting up IGMP Snooping on each network segment and ensuring that they are all appropriately coordinated.
In a VLAN environment, it’s essential to ensure that IGMP Snooping is functioning properly. This involves checking that multicast traffic is being forwarded correctly to the relevant VLANs and that the IGMP Querier is correctly identifying multicast group memberships within each VLAN.
——
While Internet Group Management Protocol (IGMP) Snooping is a valuable networking technique for optimizing multicast traffic, it also presents several challenges that need to be addressed. These challenges can vary from addressing issues in Layer 2 vs. Layer 3 networks, managing IGMPv2 and IGMPv3 messages in mixed protocol environments, troubleshooting IGMP Snooping on network switches, resolving multicast group communication problems, to ensuring compatibility and interoperability of IGMP Snooping in a network.
IGMP Snooping operates at Layer 2 of the OSI model. However, specific challenges may arise when implementing IGMP Snooping on Layer 3 networks. One such challenge could be the inappropriate forwarding of multicast traffic due to the absence of Layer 2 IGMP information. To address this, network administrators can use techniques like Protocol Independent Multicast (PIM) and Multicast Listener Discovery (MLD) Snooping.
In a mixed protocol environment, handling both IGMPv2 and IGMPv3 messages can be challenging. This is because IGMPv3 offers advanced features not available in IGMPv2, such as source-specific multicast. To address this, network switches should be configured to support both versions and correctly interpret their messages.
Troubleshooting IGMP Snooping on network switches involves identifying and resolving issues that prevent the correct operation of IGMP Snooping. This could include checking the switch’s configuration, verifying the IGMP Snooping table, and monitoring IGMP messages. Regular network audits and proactive monitoring can help in early detection and resolution of these issues.
Multicast group communication problems can occur due to incorrect IGMP Snooping configuration or network issues. These problems can be resolved by ensuring that the IGMP Querier is correctly configured and that multicast traffic is being forwarded correctly. Additionally, network administrators should regularly monitor the multicast group membership table for any inconsistencies.
Ensuring compatibility and interoperability of IGMP Snooping in a network is crucial for its successful implementation. This involves making sure that all network devices support IGMP Snooping and can correctly interpret IGMP messages. Furthermore, it’s essential to ensure that the network’s configuration is consistent and that all network devices are properly synchronized.
——
Internet Group Management Protocol (IGMP) Snooping is a sophisticated networking technique that plays a crucial role in managing and optimizing multicast traffic within a Local Area Network (LAN). This article will delve into some advanced concepts and best practices associated with IGMP Snooping, including enhancing multicast performance with IGMP Snooping Queriers, optimizing large-scale multicast environments, integrating it with multicast routing, maximizing network efficiency through customized configurations, and future trends in IGMP Snooping for network optimization.
IGMP Snooping Queriers play a vital role in enhancing multicast performance. They send out periodic queries to determine which hosts belong to a specific multicast group. This information enables the switch to make intelligent forwarding decisions, thus boosting the overall multicast performance. Therefore, it’s crucial to ensure that the IGMP Snooping Querier is correctly configured and functioning optimally.
Large-scale multicast environments pose unique challenges due to the sheer volume of multicast groups and traffic. However, IGMP Snooping can be optimized to handle these challenges efficiently. This involves fine-tuning various parameters, such as the query interval, response time, and group membership intervals, depending on the size and requirements of the network.
The integration of IGMP Snooping with multicast routing protocols like Protocol Independent Multicast (PIM) can significantly enhance the efficiency of multicast communication. This integration allows for more precise control over multicast traffic routing, ensuring that it is delivered only to the intended recipients, thereby minimizing network congestion and maximizing bandwidth utilization.
Customizing IGMP Snooping configurations based on the specific needs and characteristics of the network can significantly maximize network efficiency. This could involve enabling or disabling certain features, adjusting timers, and configuring group membership limits. Regular monitoring and fine-tuning of these configurations can ensure optimal network performance.
As networking technology continues to evolve, IGMP Snooping is also expected to see new trends and developments aimed at optimizing network performance. These could include enhanced support for more recent versions of IGMP, more advanced multicast group management features, improved interoperability with other networking protocols, and more sophisticated troubleshooting tools. Staying abreast of these trends will be crucial for network administrators to maximize the benefits of IGMP Snooping.
——
A: IGMP snooping facilitates a switch’s capacity to limit multicast traffic by listening to the IGMP communication between hosts and routers. This feature enables the selective forwarding of multicast traffic for improved network efficiency.
A: Routers contribute to IGMP snooping by sending IGMP queries to identify hosts interested in particular multicast traffic. The data from these queries aids in making network traffic forwarding decisions.
A: IGMP messages, encompassing query, report, and leave messages, are examined by IGMP snooping to map multicast group memberships. This map aids in the intelligent forwarding of multicast traffic.
A: Activating IGMP snooping results in reduced multicast traffic, improved bandwidth utilization, and decreased network congestion. It also prevents unnecessary multicast packet flooding, thereby boosting network performance.
A: The IGMP snooping queried, a function within a switch, sends IGMP general queries to ascertain which hosts maintain interest in multicast traffic. It plays a vital role in maintaining an accurate map of group memberships and efficient traffic forwarding.
A: IGMP snooping processes IGMP reports or leaves messages sent by a host when it joins or leaves a multicast group. This allows for the update of the forwarding table and adjustment of the multicast traffic flow.
A: IGMP snooping is a standard feature supported by modern managed switches and routers. It is crucial for devices that must handle multicast traffic efficiently in networking scenarios.
A: Yes, IGMP snooping can bolster network security by preventing multicast traffic from being forwarded to unauthorized ports, thus aiding in the isolation and protection of sensitive network information.
A: IGMP snooping analyzes IGMP packets to monitor group membership reports and multicast traffic needs. This analysis allows the switch to make informed decisions about multicast traffic forwarding.
A: Yes, IGMP snooping is a crucial tool for managing multicast traffic within a local network. It ensures that multicast packets are only forwarded to ports that have expressed interest in receiving them, thereby optimizing network performance.
——