Stateful Packet Inspection (SPI) firewalls are crucial for protecting contemporary networks from ever-growing cyber threats. Traditional firewalls use heuristics on traffic patterns and simply block or allow certain patterns of traffic based on pre-determined criteria. Unlike these ‘dumb’ firewalls, SPI firewalls look into the context and ‘state’ of packets as they flow through the network. This added ‘intelligence’ makes it possible to be block activities with much more accuracy, increasings the layer of security provided. This article will delve into the inner workings of stateful packet inspection, its merits over other firewall technologies, and its role in protecting sensitive information, and the need to maintain the sanctity of enterprise networks. Regardless of whether you are an IT expert or just someone looking to broaden your knowledge of cybersecurity, this guide intends to explain how SPI firewalls function and their importance in protecting modern networks and elaborate their significance in contemporary cyber protection measures.
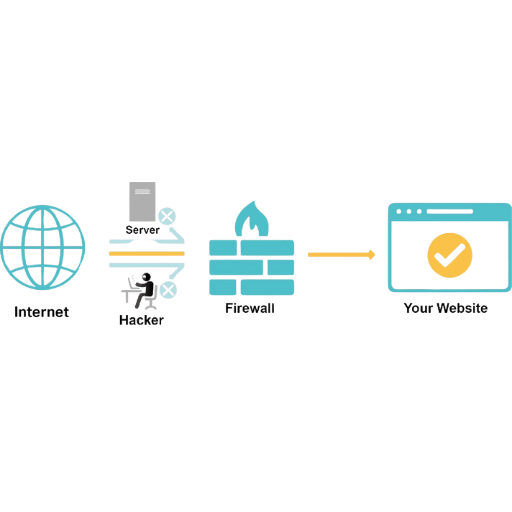
A stateful packet inspection (SPI) firewall is a type of network security device that monitors and controls traffic based on network-specific policies. Unlike simpler firewalls, SPI firewalls track the status of connections and scrutinize data packets to ensure they are part of an established session. This means that traffic which is sent or received is validated against expected parameters; anything suspicious or harmful is isolated. In contrast to older methods of packet filtering, SPI firewalls provide greater protection by observing the context and state of the connections made on the network.
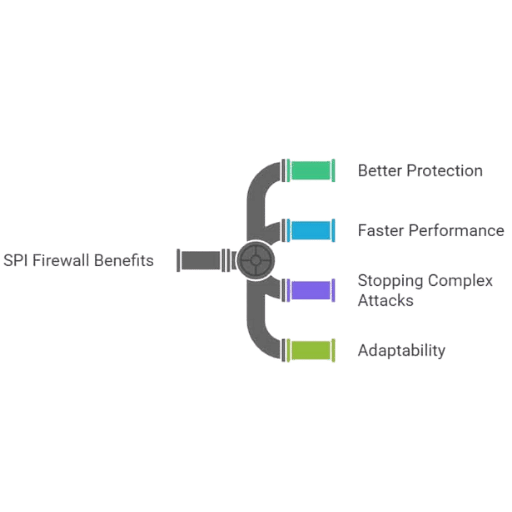
Stateful packet inspection (SPI) firewalls are capable of tracking active connections allowing them to recognize whether certain traffic is legitimate and close some older connections. Conversely, stateless firewalls look for some data within data packets without the context of the connection being made, resulting in a one-sided judgement and analysis.
The difference between the two types of firewalls is their capability. SPI firewalls offer higher protection by evaluating the traffic context of the network, preventing even more complex attacks. Whereas, stateless firewalls do not keep any connection information, making them faster, but less accurate in detecting security threats.
As noted above, the comprehensive integration of routers and firewalls at the system level optimizes the two essential aspects of the entire network: security and performance.
Dynamic packet filtering works to enhance security by reinforcing boundaries based on active sessions, filtering incoming and outbound data packets, and monitoring active connections. Each packet’s header is checked for the sender, receiver, service, and policy along with relevant protocols, and it is examined against the stated policies in the security framework. It also checks the session state to allow only packets marked as expected and authorized. It provides solid protection by blocking default packets, protecting the network from unauthorized access and spoofing attacks.
Network traffic and security functions are adjusted using predefined rules. Step-by-step guides assist with the control of security parameters set by firewalls which verify organizational protocols and enable seamless network performance. These data packet restrictions that firewalls impose are determined based on src address, dst address, service port, and type of policy regarding protocol. Rules may vary as policies shift. According to configuration, rules may be dynamic or static which enables adapting to changes in traffic or the presence of new threats.
A well-crafted set of rules can help reduce latency by filtering out non-essential traffic and ensuring that critical applications are given priority. For example, research shows that firewalls located at the application layer can block as much as 95 percent of malicious traffic before it reaches end-user systems, greatly reducing security risks. In addition, more sophisticated firewalls use machine learning to identify and prevent anomalous traffic, improving the accuracy of detection by applying historical and behavioral data against the system’s baseline.
Also, firewall rules affect network scalability. For instance, organizations using cloud infrastructure must be careful to coordinate their firewall rules with the active allocation of resources to prevent disruptions. Effective rule optimization such as removing redundant rules or ignoring some protocols can improve network performance by up to 30 percent according to industry standards. This warrants routine audits of the firewalls to remove outdated or conflicting rules that couldwithin weaken security posture or cause latency-induced network slowdowns.
As such, cybersecurity protocols designed around firewalls must take traffic rules into account because they can promote or hinder multi-faceted balanced navigation accuracy during network access.

There are many categories of firewalls, each serving its own distinct purpose in safeguarding networks.
All types of firewalls serve specific needs. Most Organizations tend to use a single type or a mix of types depending on the architecture of their network and its security needs.
Examining the payload of packets as opposed to merely scrutinizing their headers enables advanced traffic analysis known as Deep Packet Inspection, or DPI. This form of analysis is one of the core functions of firewalls today. Deep granular inspection allows firewalls to detect and control particular applications, protocols and even certain potential threats within network traffic.
One of the most important advantages of DPI is its ability to uncover sophisticated cyber threats to security such as malware, ransomware, and phishing attempts that tend to get past traditional security protocols. Recent data from cybersecurity indicates the number of incidents involving malware and encrypted traffic has increased to over twenty percent in the past year. This shows how vital tools such as DPI that can inspect and secure traffic are. Moreover, DPI helps enforce application level policies like control and restriction of bandwidth and blocking of some applications which improves network performance and posture.
Nevertheless, applying DPI has its challenges. The latency added by in-depth inspections can be problematic in environments requiring high throughput. To mitigate these issues, many organizations use firewalls with built-in hardware acceleration or parallelize algorithms within the DPI software. Regardless of such hurdles, as immediately evident from the more than 80% Internet traffic quoted by recent studies, encrypted traffic poses a significant challenge for the dynamic shifting torrent of Internet threats and makes the case for DPI being the ongoing warhead of network security.
When appropriately followed, such configurations will improve overall network security, while also ensuring strong configuration avoidance errors.
Integrating antivirus software with your SPI firewall boosts network security by adding another layer of defense against viruses and other forms of attacks. The antivirus software checks files for threats before sending and receiving them and helps the firewall with its packet filtering. For proper integration, purchase antivirus software that will work with your firewall, and set both up to avoid working at cross purposes. Ensure that antivirus definitions are updated on a regular basis to avert emerging threats, and occasionally check the system to validate its functional reliability. This approach enhances a network’s holistic security posture.
Shoring up infrastructure is crucial for increasing defenses against cyber threats. One such advancement is the adoption of sophisticated network segmentation that locked critical resources and sensitive data into distinct protected zones. Recent reports from industry research suggest that segmentation may curtail the chances of an attacker moving laterally within a system by close to 75%, substantially limiting the damage that breaches may cause.
Enhancing the system can be achieved by implementing Software-Defined Networking (SDN). With SDN, control of traffic in the entire network can be managed from a single point, which allows for fast reactions to attacks with the application of flexible policies and active threat management. Incorporation of Artificial Intelligence into Intrusion Detection and Prevention Systems (IDPS) helps to enhance monitoring and recovery processes because these systems are able to learn and identify threats and neutralize them in real-time.
As well, making use of encrypted communication protocols like TLS or HTTPS not only allows encryption to be maintained, but also reinforces the power of soft ensuring that the data remains fully secured. With studies showing 70% of cyberattacks targeting data while in transit, the implementation of these protocols is important to guard sensitive data.
Vulnerability monitoring, along with constant review and change of network hardware like switches and routers, enhances security. Newer versions of such equipment comes with extra protective tools such as firewalls, access control lists (ACLs), and nonmanual combating of exploiting weaknesses updating causing uncontrolled attacks. Integrating these improvements in infrastructure with vigilant supervision and optimization creates a solid and reliable secured network setting.
While assessing requirements for network security, begin with estimating the scale and level of intricacy within your network. Analyze the amount of data traffic and the sensitivity of the information being transmitted to verify whether adequate protection is provided home security. Evaluate probable dangers that pertain to your industry or environment since different sectors have different threats. It is equally important to think through compliance requirements as GDPR, or HIPAA, which may stipulate particular security measures. Lastly, make sure the selected firewall maintains adequate protection against potential changes, provides flexible scaling and growth opportunities, and integrates into the existing infrastructure for simplified management.
A firewall suited to the type of bloodless warfare waged against the hacker’s network is the deadliest tool available. Strategies involving phishing, DDoSing, infecting networks with worms and malware, or even zero-day exploits need more aggressive defense mechanisms at the very minimum.
There is a rise in DDoS attacks, which are inflicted by flooding a network with traffic to make it idle, and require firewalls equipped with IPS and real-time traffic analysis features. Peak attack sizes now reach 800Gbps in volume. All capable firewalls should block this traffic without straining access for verifying users. Research states the global rate for DDoSDDoS attacks raises by 22% every year.
In terms of data breaches, malware attacks rank first, amounting to 35%. This requires firewalls with deep packet inspection (DPI) capabilities and antivirus integration to remove malicious files before they damage the system. Ransomware also requires special crafted solutions to contain the issue, affecting firms every 11 seconds around the globe.
Phishing attacks highlight the attention towards financial information while aspiring to retrieve login details. Firewalls also need to provide DNS filtering along with anti-spoofing features. Furthermore, firewalls equipped with threat intelligence as well as machine learning algorithms become important in dealing with zero-day exploits.
Configuring a firewall requires aligning security measures with an organization’s specific threat landscape. Investment in next generation firewalls is essential due to application awareness, secure remote access, and advanced traffic filtering capabilities, which aid businesses in mitigating modern threats effectively without hindering operational efficiency.
A: An SPI Firewall scrutinizes data packets at their reception by checking their source and destination IPs as well as their port numbers and other protocol specific details. It manages network connections between endpoints using a state table to determine whether a connection can be made or whether a certain packet has to be dropped. This is done against baseline policies in conjunction with the current state of the connection in question.
A: Of course, it’s possible. An SPI firewall works by controlling the traffic a server receives. By studying the patterns of the data being sent in and watching changes in the state of the connection, the firewall is capable of blocking any connection which seems to be attacking the server with DDoS traffic. There are other such some other SPI firewalls that are more sophisticated like those made by Check Point Software that focus on preventing DDoS attacks.
A: An SPI firewall interprets data contained in a given packet by checking sectional constituents of the packet including its header and payload. It examines the type of protocol in use, the source and destination, and the order in which packets have been given. This enables the firewall to conduct examination increases the chances of identifying malware or unauthorized access attempts.
A: Malware protection offered by an SPI firewall is provided through scanning incoming packets for known malicious signatures or suspicious behaviors. Such firewalls can block the download of infected files, terminate connections to known malware command and control servers, and prevent the execution of hostile processes. Some more advanced versions of SPI firewalls also use the databases of antivirus programs to bolster the detection of malware.
A: Blocking and allowing of packets is done by comparing them against a certain predetermined set of instructions, or heuristics governing decision criteria for specific packets. These instructions are hypotheses about the source and destination IP address, the port number, and the type of protocol used. The firewall verifies the status of the network connections to confirm that incoming traffic is actually from active connections.
A: The use of an SPI firewall to protect your home network has many benefits such as better security against cyber attacks, protection from malware and unauthorized access, malware protection, and better overall performance of the network. Many home routers serve as an example, TP-Link Archer A6 comes with integrated firewalls that can block DoS attacks and provide protection to your devices and data from a variety of online threats.
A: An SPI firewall varies from other types of firewalls by keeping state information of certain active connections such as ongoing calls. Unlike more basic firewalls that only filter packets sent, an SPI firewall is able to examine the entirety of the connection including its state. This permits better decisions to be made and enhanced protection against intricate attacks. Generally speaking, SPI firewalls tend to out perform more static firewalls but they may underperform in complexity when compared to next generation firewalls.
A: In the selection and deployment of network firewalls, relevant factors like the adequacy of protection required, network performance requirements, growth potential, administrative workload, and compatibility with other security solutions are critical. It is also required to determine what particular threats your network is exposed to, the kind of applications and services that are in use, and any applicable compliance policies. The range of options available are quite numerous, each with its drawbacks and benefits, which include SPI firewalls. The selection, however, depends on your particular security requirements and existing infrastructure.
1. Evolution of Firewalls: Toward Securer Network Using Next Generation Firewall
2. Study of Personal-Firewall Technology and Preventive Measures
3. Design and Application of Individual Firewalls Based on Packet Filtering Windows 2000/XP