The changing technological landscape has recently transformed the process of video surveillance, making Video Management Software (VMS) a vital part of contemporary security frameworks. As organizations look towards 2025, emphasis is on advanced VMS systems with features such as AI analytics, cloud support, and expandable frameworks. This article will analyze how these system options will compare in their core capabilities and modern day surveillance features, describing the best VMS available in 2025. This comprehensive guide will assist you in making an informed decision whether you need to upgrade the system or if you need a new solution for enhanced operational efficiency.
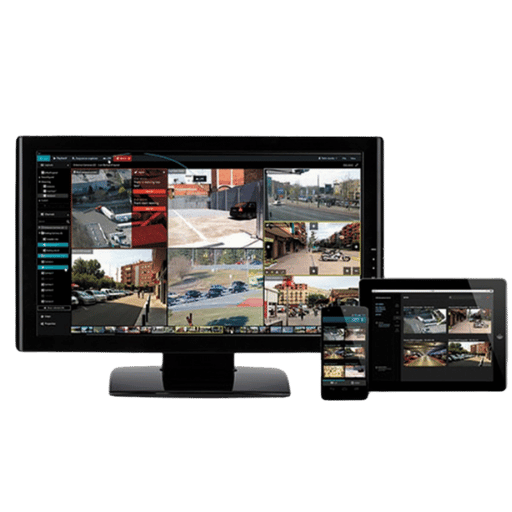
A surveillance software system called video management software (VMS) processes and saves footage from surveillance cameras. Organizing video files for easy access involves recording, tagging, and archiving video footage as well as providing monitoring access through live feeds. VMS systems enhance security through alarm customizations, motion-activated video recording, and intuitive user interfaces. Enhanced situation awareness and peace of mind is made possible through modern surveillance technology that integrates video management capabilities, making these systems indispensable tools for security operations.
Video Surveillance and Security Works In Association with VMS by acting as a central point for the management and analysis of video data and restricting access to the recorded video footage. Cameras capture live footage which is streamed to the VMS for storage or monitoring. For monitoring, the VMS facilitates smooth operational integration of its components by permitting the combination of video feeds with motion detection devices and event hypotheses. With the addition of User defined alerts, video tuning becomes elevating the level of awareness and understanding cultivated by a specific situation – situational awareness. Moreover, the VMS provides other peripherals like access control systems and various other security devices for a holistic approach towards asset surveillance and protection.
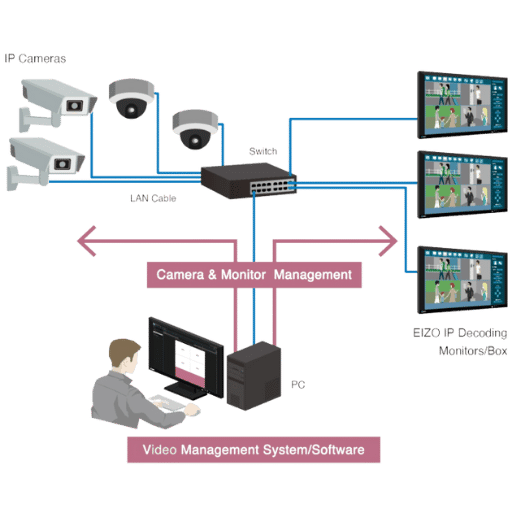
Certain primary elements must be taken into account while selecting a VMS:
The following factors reveal important differentiations among Video Management Systems (VMS) Platforms:
The effectiveness of each system differs based on the user’s specific security needs and operational scope.
These providers are known for their innovative approaches, custom designs, and responsiveness to different levels of security challenges.
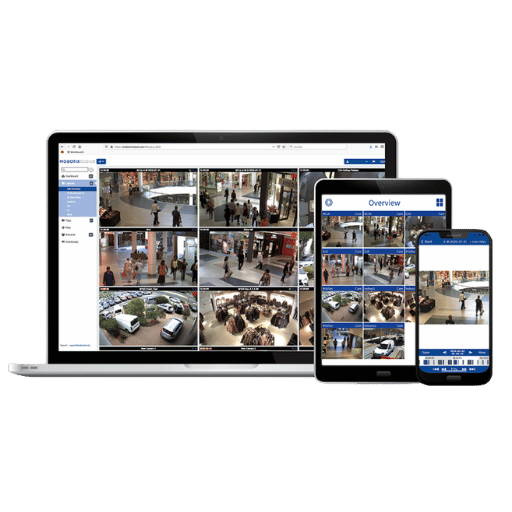
Cloud technologies qualitatively changed Video Management Systems (VMS) because of their ease of scaling, increasing accessibility, and cost savings. This enable users to retrieve and manage video data using the Internet, eliminating the need for costly hardware installation at the premises. Flexibility to view footage through any internet-enabled device enhances real-time interaction and reaction. Moreover, cloud-enabled VMS usually comes with additional AI analytics and update features which make them safe and current. Such developments have made cloud based VMS a go-to option for enterprises which need convenient and robust surveillance solutions.
Modern surveillance systems have greatly benefitted from the implementation of Artificial Intelligence (AI), which enhanced precision and performance to unfathomable levels. AI enabled surveillance technologies capture video footage through surveillance cameras and use algorithms to scrutinize that video footage in real time. This enables more automated features such as detecting unauthorized access, abnormal activities, or any suspicious elements that greatly reduces the human dependency.
Facial recognition technology represents one of the most significant advancements in AI. Studies show that modern AI technologies are capable of recognizing people with 99.7% accuracy under ideal conditions. The integration of AI further facilitates object, behavior, and even license plate recognition, which aids in the protection of people and infrastructure.
Predictive analytics is another feature that changes the game. AI-equipped systems can sift through historical surveillance footage to assess potential breaches in security. For example, assessing crowd density in public areas can ward off potential problems associated with overcrowding or stampedes.
AI video analytics further improve data retention and bandwidth costs by filtering out unimportant information, which optimizes storage and transmission. In turn, this results in reduced expenses for businesses and enhanced efficiency for the systems. In addition, systems have progressively incorporated Natural Language Processing (NLP) or speech recognition functionality, allowing the setting of alerts or notifications to specific sounds, as well as command activation through voice.
Surveillance is expected to adopt AI tools more broadly alongside advancements in video analytics, which is expected to exceed 21 billion dollars by 2026. There is emerging demand that needs to be catered to in smart cities, retail, and critical infrastructure that would help maintain security and situational awareness. These innovations undoubtably cover important ethical and privacy issues alongside the need for regulations concerning responsible use.
The expectation is that by 2025, there will be markable improvements on AI and ML powered video surveillance systems that would allow for decision making and real time analytics, integration with edge computing, and reduced latency. These advancements will also be accompanied with sharper object tracking and identification due to enhanced 4k and 8k resolution. There will also be a shift towards cloud solutions that store massive amounts of video data and can easily be adapted to changes, while privacy preserving methods like federated learning are expected to gain traction because of the increased need for protecting data. All of these trends are aimed towards striking a balance between functionality and ethical video surveillance.

Melding an organization’s existing security infrastructure with a Video Management System (VMS) poses both technical and operational challenges. One notable challenge is compatibility conflicts with pre-existing hardware and firmware components; new VMS platforms may not be compatible with legacy systems. Older cameras and devices may use outdated firmware or protocols (such as ONVIF compliance), which require expensive upgrades or replacements in order to be integrated seamlessly.
Another barrier is the limitation on data management and storage. Cutting-edge VMS solutions create gargantuan amounts of video data, creating severe strain on storage systems. Organizations with limited storage infrastructure may experience constraints in retention periods or video quality. Research shows that the global video surveillance storage market is anticipated to increase at a Compound Annual Growth Rate (CAGR) of 18.4% between the years 2023 and 2030, showcasing the dire need for sophisticated storage capabilities.
Other severe issues include limited Network Bandwidth: gaps in the available network bandwidth can be problematic especially when multiple high-definition cameras are connected to pre-existing networks. Streaming HD or 4K video requires a lot of bandwidth which may cripple older network architecture or inadequately scaled systems, causing latency or dropped frames. To counter these issues, organizations need to optimize bandwidth use or upgrade their networks.
As systems become increasingly interconnected, operationally cybersecurity risks are becoming a significant concern. According to a report by cybersecurity professionals in 2023, more than 70% of security systems are susceptible to attacks due to insufficient credentials or outdated software. To mitigate these attacks, proper system configuration, encryption, and VMS-enabled infrastructure maintenance are essential.
Moreover, under the heading of “User Adoption,” training and integration barriers can impede smooth integration. Some employees that are used to working with older systems may not be able to use new tools proficiently. Therefore, training and adequate assistance must be provided in order to help the employees use these systems, circumventing operational ineffectiveness.
To mitigate these problems, there must be advance planning with collaboration across multiple disciplines, alongside investing in new technologies and developing existing human resources to achieve thorough and effective VMS integration.
In guarantee flexibility and seamless expansion in VMS tools, I make sure they focus on a modular structure that meets changing needs design and plan for future changes. By choosing technologies that enable integration and interoperability, I can expand functionalities while ensuring existing operations are not disrupted. Moreover, where appropriate, I concentrate on using cloud-based solutions because they have higher flexibility, access, and resource optimization. Evaluating system performance and capacity continuously enables me to manage constraints in a proactive manner ensuring the VMS is aligned with organizational needs.
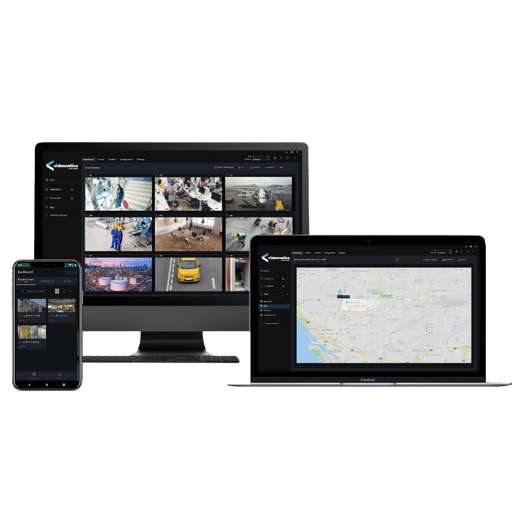
The remote access feature in video management systems enhances security by allowing monitoring and response to incidents from almost any location in real-time. Thus, security personnel can manage different incidents due to their remote access and do not have to be physically present, which increases operational efficiency. Moreover, the remote access feature allows for centralized management of several sites, which simplifies the problem of monitoring many buildings spread across different locations. With secure authentication methods and encrypted connections, remote access can help protect sensitive video footage while allowing access to those who have authority.
Modern VMSes are equipped with mobile applications and tools for remote monitoring. These modern video management system applications grant users access to live video feeds, video playback, and alert notifications via smartphones and tablets. Some of these well-known software solutions are Milestone mobile, Hik-Connect, and Avigilon Control Center Mobile, which are all user-friendly and accessible. Two-factor authentication and encrypted data transmission enable security while still ensuring remote actionable data insight from these mobile applications. Organizations are no longer required to be at a physical control room and can utilize these tools to have constant situational awareness and react promptly to events whenever anywhere.
Security within organizations can remain high in the presence of remote capabilities by implementing strong verification techniques like multi-factor authentication (MFA) and role-based access control. These measures protect the system from unauthorized access by ensuring that only personnel with the appropriate authority can access the system. These measures, combined with encrypted data transfer, further mitigate the risk of sensitive information being compromised. Moreover, automatic software updates are essential to resolve vulnerabilities and ensure the system is always fortified against other potential threats. Remote monitoring tools, designed with intuitive interfaces, allow for swift incident response when coupled with customizable alert thresholds, minimizing risk while optimizing operational efficiency.
A: The superb video surveillance software for 2025 contains enhanced versions of VMS systems from Milestone, Hikvision, and even Verkada. The top video surveillance platforms now contain AI video analytics, cloud storage, and even IP camera support. The outstanding video management solutions tend to have scalable architecture for all levels of a business while simultaneously reinforcing physical security with automated alerts, real-time monitoring, and full integration with other systems such as access control.
A: In terms of openness, Milestone XProtect performs remarkably well among the competitors of CCTV management platforms. The system possesses an open platform structure with the ability to customize to thousands of cameras and security devices. In terms of greater levels of flexibility, the company has mastered scalability from smaller installations to enterprise level with the system. With excellent video evidence management comes advanced analytics software as well, not to forget the surveillance management tools offered. Yes, other competitors like Hikvision offer lower prices, but Milestone’s flexibility stands out. For 2025, Milestone will still retain the top position because of third party options, continuous updates, and endless integration options.
A: Like any service offered on the cloud, VSaaS (Video Surveillance as a Service) possesses numerous advantages for security operations today. Unlike traditional NVR systems, Cloud Video Management Systems NVRs are virtual, thereby alleviating capital and maintenance costs tied to on-site hardware. These systems offer remote access to video footage, automatic software updates, ranging and adaptable cloud storage, and scalable resources that adjust to meet your requirements. Other advantages include enhanced recovery from disasters, easier management of multiple sites, improved cybersecurity measures, and seamless advanced AI video analytics integration. In 2025, leading VSaaS provider will offer essential modern security operations encryption, redundancy and compliance functionalities.
A: Network video recorders (NVR) continue to be critical components of modern surveillance systems as they serve as the main interface for IP camera operation and video storage. Despite the acceptance of cloud-based solutions, NVRs still provide benefits such as local storage without bandwidth limitations, decreased long-term expenses relative to subscription services, independent functionality during internet outages, and uninterrupted data recording. Advanced NVR systems today provide enhanced compression technologies, Ai-driven video analytics, and interoperability with other systems for total security management. For organizations that have data sovereignty constraints, or that have limited internet access, NVR technology paired with cloud-storage backup hybrid solutions offer the most comprehensive approach to video surveillance software implementation.
A: Start with interfaces optimized for user interaction together with Mobile Applications tailored for convenience. These accompanied by strong surveillance alert management should take priority in mobile surveillance management software in 2025. Moreover, advanced VMS systems should include support for high resolution IP cameras, advanced evidence retrieval search capabilities, flexible storage (cloud and on-premise), speedy retrieval of video evidence, and offer advanced evidence search functionalities. The best now include AI analytic capabilities for object detection, behavior detection, and automatic incident classification. Health monitoring of the system, control over user’s credentials, issues cybersecurity, and network access controls technologies with external physical security systems through open APIs are additional crucial attributes.
A: Modern VMS platforms are now integrating a plethora of sensors to form an all-inclusive security system. Such integrations comprise motion sensors that activate recording or alerts, environmental sensors that track changes in temperature or humidity, audio sensors that pick up sounds such as glass breaking and other strange noises, and perimeter sensors that fortify boundary protection. By 2025, Advanced VMS systems use these sensor inputs to provide contextual information related to the video content, mitigate false triggers through multi-tiered verification, and execute pre-defined actions pertinent to sensor activations. Through this approach, surveillance systems become intertwined with artificial intelligence to distinguish between activities and security threats that necessitate physical intervention, thus significantly enhancing physical security measures.
A: With the introduction of network video protocols, surveillance at enterprises has been greatly streamlined with the ability to control communication standardization between IP cameras, recording devices and management software. These protocols allow for the transmission of higher resolution videos, more efficient use of bandwidth, and stronger cybersecurity measures through video encryption. Enterprise businesses are able to take advantage of network video standards, like ONVIF, that provide interoperability within systems from different manufacturers – making it easier for clients to design their systems without the consequences of vendor lock-in. Moreover, advanced implementations through 2025 will also include adaptive streaming according to available bandwidth, processing analytics on the edge, and the simplified deployment through Power over Ethernet (PoE), positioning these as foundational elements in any modern surveillance system management strategy.
A: The response to security breaches has been improved tremendously by cloud-based alert systems as they analyze video footage and surveillance data in real-time. These systems are capable of sending real-time notifications to security staff when certain events (AI analytics ‘suspicious activity’, unpermitted entry, object removal etc.) of interest take place. The cloud infrastructure allows for the possibility of email, SMS, VoIP, smartphone apps, automated alerts, and interaction with central monitoring stations as a gateway for multiple alerts. Other sophisticated features of advanced alerts include customizable alert priorities, time-dependent scheduled rules for alerts, and correlation of multiple events that can lead to unnecessary nonresponsive alerts. Provided there are no deep-reaching functional gaps, these alert systems are capable of responding efficiently given they monitor and track the secure incidents while ensuring audit trails of notifications and actions taken post alarms are present.
A: AI technollgoy has penetrated every industry including video surveillance systems. AI’s introduction has revolutionized passive video monitoring camera systems into active security measures. In the best surveillance technology modules by 2025, AI is capable of identifying advanced object classification like distinguishing people from other vehicles, further segments, and numerous nonliving objects with high precision. AI algorithms offer suspicious activity detection and analysis such as detecting unattended objects, fuselage fortification, and assessing overpopulation. In addition to security measures, these systems provide face recognition (where legally allowed)s, license tag identification, and visitor quantification that provide significant intra-business intel. The most direct integration of AI features include foreseeing analytics where AI can track active security issues getting out of hand before they fully inflow. Hence it becomes clear that artificial intelligence becomes one crucial factor needed to be incorporated in any sophisticated video surveillance programs advanced after surveillance software.
1. The Intelligent Video Management System: A Use Case of Software Defined Class
2. Video Quality Management over the Software Defined Networking
3. Joint Resource Allocation and Traffic Management for Cloud Video Distribution over Software-Defined Networks
4. A Quality of Experience Management Method For Intent-Based Software-Defined Networks
5. On the Use of Deep Learning for Video Classification
6. Surveillance